|
Human centered-design What is human-centered design?Click to read
 Human-centered design is a creative approach to problem-solving. It is a process that puts the people you are designing for, along with their needs, attitudes, experiences, and beliefs, at the center. In human-centered design, the audience is usually referred to as the user. The process culminates in the creation of a new solution that has been tailored to the needs, attitudes, experiences, and beliefs of the recipient. This is only possible by focusing on the user, empathy, active listening, and then generating ideas and building lots of prototypes. Relevant links: Ideo > Tools (https://www.ideo.org/tools); Design Kit > What is Human-Centered Design? (https://www.designkit.org/human-centered-design) The human-centered design consists of three phases:
How will you know that the solution is indeed human-centered design?If the people you want to create for have been at the center of the process all along, and the final solution meets their needs, then it is definitely human-centered design But what about the company's priorities?After all, every company has its own priorities. Not all of them coincide with what the user wants. What do you run your business for? Do you want a stable life, a good income, or maybe you want to pursue your dreams? Whatever it is, there's nothing wrong with putting your business priorities and your team, not the user, at the center. So is human-centered design a utopia?No. Today's business must take care of the user, and human-centered design is one of the most effective ways to do that. However, running a business is not a "users or me" choice. Are you asking yourself who is more important: the user or you? Human-centered design or company priorities? Well, it's a no-win dilemma. Without the user, there is no company. Without your company, there is no product, service, or user. You should strike a balance and take care of yourself as well. In the following section, you'll find guidelines for using human-centered design in the context of cybersecurity, without compromising your company's priorities. How to use human-centered design in you cybersecurity management plan?Click to read
 As we said, human-centered design is successful mostly thanks to empathizing with the user. People need your attention, need to feel the company cares about them and their values. So let's think about those values. Most users need to feel safe in the online environment. Remember that pandemic has caused that millions of new people start to work, buy and communicate online. So for them, the online environment is something new, they need to feel safe more than others. Their trust in your company on the Internet may be much more fragile than those who are used to e-commerce. So what you need is to build a safe website, platform and/ or software for your users. You must find all bugs as soon as possible — here you can use human-centered design. Where to start?Use the model of a bug bounty program. Bug bounty What is bug bounty?Click to read
 A bug bounty is a program offered by many companies, websites, organizations, and software developers. It relies on end-users to recognize bugs (especially those concerning security exploits and vulnerabilities) and report them to admins. This kind of program helps the company to test their products more thoroughly. Even if the company hires professional Quality Assurance personnel usually not every detail or combination can be tested before the release. More tests mean more efficiency in discovering and resolving bugs before the general public is aware of them, also, preventing abuses and hacking. However, one or even a few people can't find everything in a short time. Remember that an employee or a B2B specialist is an additional cost for your company. You can optimize time and costs by opening the bug bounty program.
How to create categories of bugs and relevant bounties?There is no one method of creating bugs' categories and assigning bounties. Everything depends on your product, website, software, and content. Take a look at a case study.
Case study: A.S Watson Group is the world's largest health and beauty retail group.Click to read
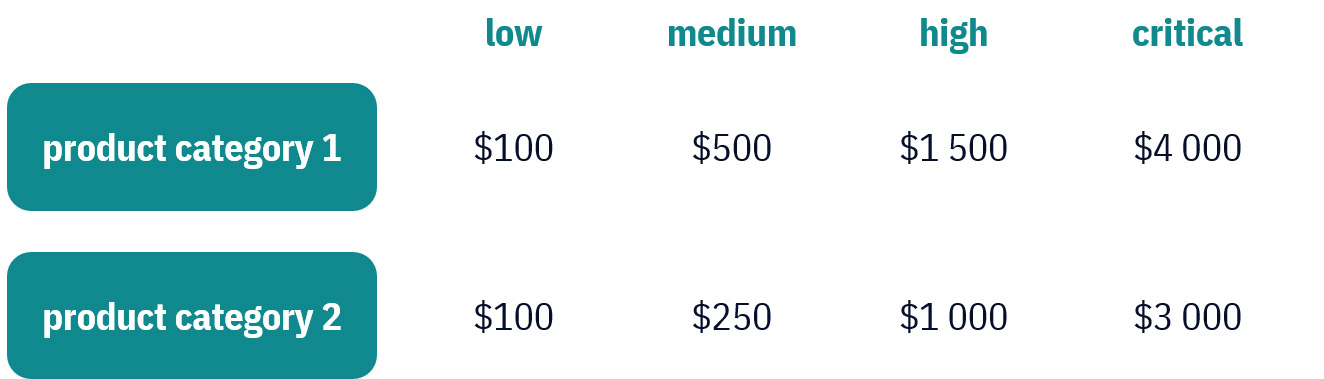
 Website: www.aswatson.com A.S. Watson opened a bug bounty program in July 2020. The goal is to make sure that the company's more popular retail websites and mobile apps are secure. A.S. Watson Group has posted information about its program on HackerOne: https://hackerone.com/watson_group?type=team&view_policy=true A.S. Watson Group operating modelEstablishing product categories The company divided the websites and apps that were included in the program into 2 categories. Next, it gave one a higher priority than the other. Establishing bug categories Not all bugs are equally important to a business, so it is important to prioritize them clearly. A.S. Watson Group has divided bugs into 4 categories:
Establishing bounties A.S. Watson Group gives rewards in the mentioned 2 product categories and according to the bug category. The amount per reported bug is $100-4000. Look at the table below.
Establishing clear channels and rules of communication The HackerOne website is a platform for companies to engage with the ethical hacking community. So A.S. Watson Group doesn't need to establish special communication channels because the platform itself already provides them. A.S. Watson Group takes full advantage of HackerOne's platform options: adding updates, notifications of changes, and showcasing the ranking of top hacks. Also, its page informs potential applicants of this:
What are the benefits to the company?
What are the benefits of an ethical hacking community?
It looks like a win-win scenario.Certainly, A.S. Watson Group cares about cyber security through its bug bounty program. Where's the human-centered design?A.S. Watson Group's bug bounty program is a perfect example of a balance between corporate priorities and human-centered design. Why? Let's take a look.
What will the company achieve thanks to ethical hacking? So who is in the center of the company's interests? What can we learn from this?Click to read

What questions should you ask yourself before you create your bug bounty program?Click to read

Look for inspirationClick to read
 There is no single way to create a good bug bounty program, and there are no exact rules for giving bounties or categorizing bugs. That's why you should look for inspiration on websites where big companies like Aliexpress, Android, Deutsche Telekom (T-mobile), and Google announce their programs. Check for example: HackerOne: https://hackerone.com/bug-bounty-programs | |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
Keywords
human-centered design; cybersecurity management plan; bug bounty program
Objectives/goals:At the end of this module the trainee will be able to: define and recognize human-centered design; find an answer for the question of what is more important: human-centered design or company priorities; use human-centered design in cybersecurity management plan; define and create a bug bounty program.
This course is about human-centered design in the context of taking care of company priorities. In the first unit, you will learn what human-centered design is and how to use it in cybersecurity management.
In the second unit, you will learn what bug bounty programs are. We will show you how to create and use them to build security in your company. You will also get practical tips based on the case study.
Ideo > Tools (https://www.ideo.org/tools)
Design Kit > What is Human-Centered Design? (https://www.designkit.org/human-centered-design)
HackerOne: https://hackerone.com/bug-bounty-programs
Related training material


 Play Audio
Play Audio