
|
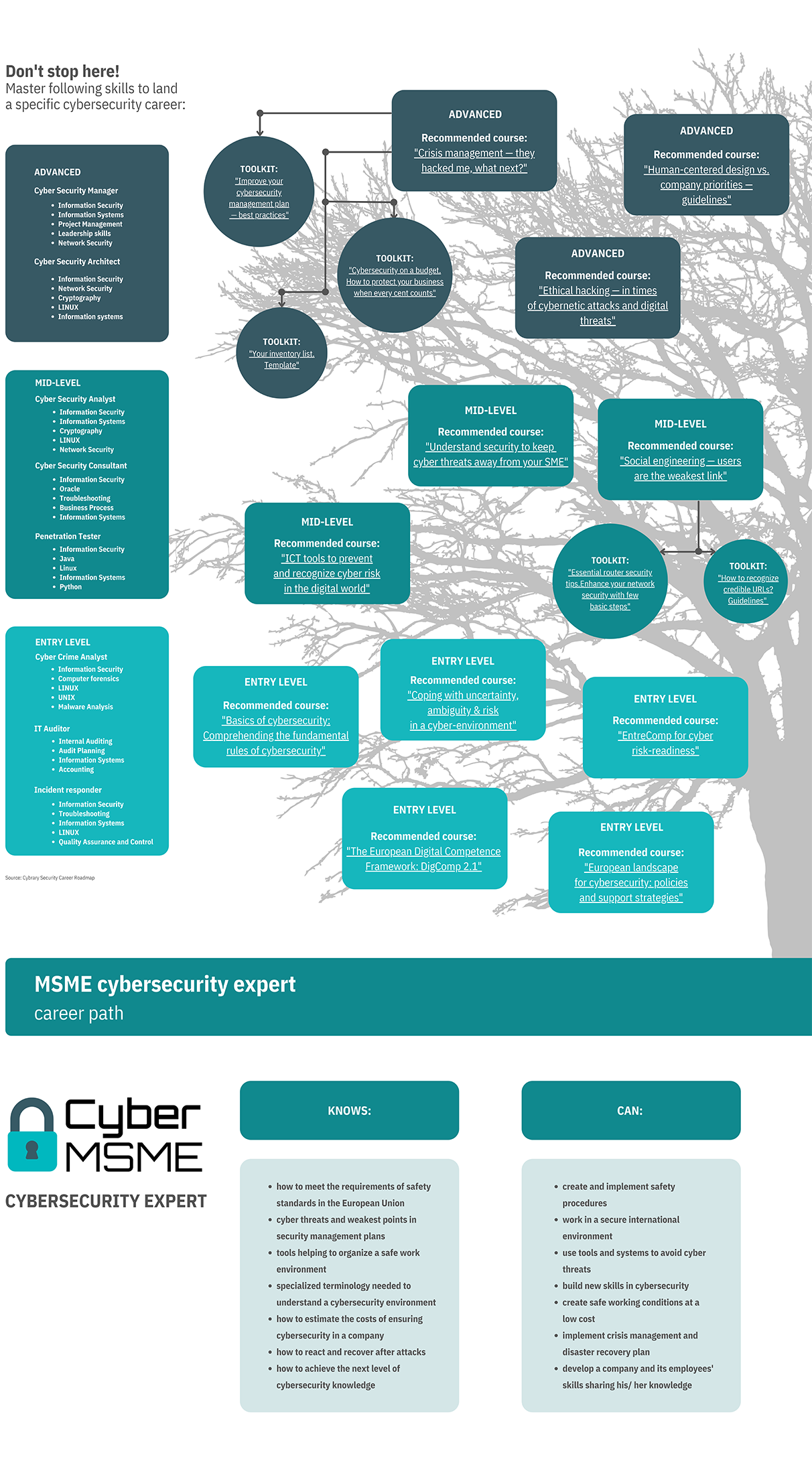
ICT Tools to prevent and recognize Cyber Risk in the Digital World In this module we will learn about the main cyber threats to SMEs and entrepreneurs before and during the Covid pandemic. We will also learn about tools to prevent and identify cyber attacks.... Go to course |

|
Basics of Cybersecurity. Comprehending the Fundamental Rules of Cybersecurity In this module we will review some of the main cyber threats to businesses. We will learn about the stages of a cyber-attack in order to be able to act in any of them. We will also learn how to protect our company from cyber attacks before, during and after they occur.... Go to course |

|
Crisis management — they hacked me, what next? This module will introduce you to cyber crisis management. In the first unit, you will get to know how to identify a crisis. In the second unit, you will receive a set of best practices for responding to a cyber crisis, whether you run a sole proprietorship or employ people. The third unit focuses on the recovery of your business after a cyber crisis. You'll get specific tips based on the case study. ... Go to course |

|
Human-centered design vs. company priorities — guidelines This course is about human-centered design in the context of taking care of company priorities. In the first unit, you will learn what human-centered design is and how to use it in cybersecurity management. In the second unit, you will learn what bug bounty programs are. We will show you how to create and use them to build security in your company. You will also get practical tips based on the case study. ... Go to course |

|
Social engineering — users are the weakest link This module is about social engineering. In the first unit, you will find a definition of the term and all the basics. In the second unit - starting from a story - we will introduce you to the techniques used by attackers. You will learn the characteristics of phishing, vishing, and baiting. In the third unit, we will summarize all the content. You will get practical tips that will help you to take care of your safety in the network. ... Go to course |

|
EntreComp for cyber risk-readiness In the context of this training module, readers will be introduced to the EntreComp Framework and how it can be of relevance for cyber security and IT proficiency. Specifically, the EntreComp Framework will be our reference model to help targets in being more responsive and alert to cyber threats, enhancing their awareness of cyber-hygiene and being overall more competitive in all domains of business. ... Go to course |

|
Coping with uncertainty, ambiguity & risk in a cyber-environment new agenda for risk management as a business functions that permeates transversely all task and activates while responding to the new urgent need of safeguarding businesses from cyber threats. We will do that by sharing trustworthy, robust and reliable managerial frameworks that applies traditionally to all business functions.... Go to course |

|
The European Digital Competence Framework: DigComp 2.1 The DigComp 2.1 looks into IT skills and digital competences in high-demand not only in the labour market, but also in all domains of civil society and active citizenship. With that said, users can work on the DigComp as a reference and support tool to reignite and foster their understanding and overall proficiency with the aforementioned 21 competences while self-assessing their progress and the ones achieved by their employees/workers. DigComp e... Go to course |

|
European landscape for cybersecurity: policies, strategies and support resources In the context of this module, readers have the opportunity to familiarise with sources and resources from EU institutions to remain updated on latest trends on cybersecurity, scale and scope of cyber hygiene domain in EU, training and education opportunities, evidence-based support material, new emerging dynamics on cybersecurity that are of relevance for businesses and organisations. ... Go to course |

|
Understand security to keep cyber threats away from your SME In today technologically evolved business landscape, there is a drastic increase in IT security breaches worldwide. As years have passed, the level of threats has also been continuously evolving, which is making it even more difficult for enterprises and government agencies to find the right cybersecurity solutions.... Go to course |

|
Ethical hacking - in times of cybernetic attacks and digital threats The course introduces the basic technical concepts behind the various stages of a hacking attack, as well as some common tools used by hackers and security professionals.... Go to course |

|
Improve your cybersecurity management plan — best practices This toolkit contains 15 best practices to help you improve your company's cybersecurity management plan. You will learn how to create strong passwords and whether a password is the best (and only) solution for protecting your data. You will get instructions on how to update the devices and software you use for business purposes. Finally, we will tell you what else you can do to protect yourself and your business.... Go to toolkit |

|
How to recognize credible URLs? Guidelines In this toolkit, you will find 5 guidelines that show you to distinguish trustworthy URLs from those that may compromise your business.... Go to toolkit |

|
Your inventory list. Template In this toolkit, you will find 6 templates for an inventory list in a table format. You can use each template for your company's use, either by editing it on your computer or printing and handwriting the data.... Go to toolkit |

|
Essential router security tips. Enhance your network security with few basic steps In this toolkit, you will find 6 simple rules to increase the security of your router — and, in addition, your entire corporate network. You don't need an expert's help to implement those tips. You can do it yourself.... Go to toolkit |

|
Cybersecurity on a budget. How to protect your business when every cent counts Description In this toolkit, you will find a set of tools to increase your online security, which we recommend especially for micro and small businesses with limited budgets. You can also use these tools for private purposes. We have selected all solutions considering the actual financial possibilities of micro and small companies. ... Go to toolkit |

